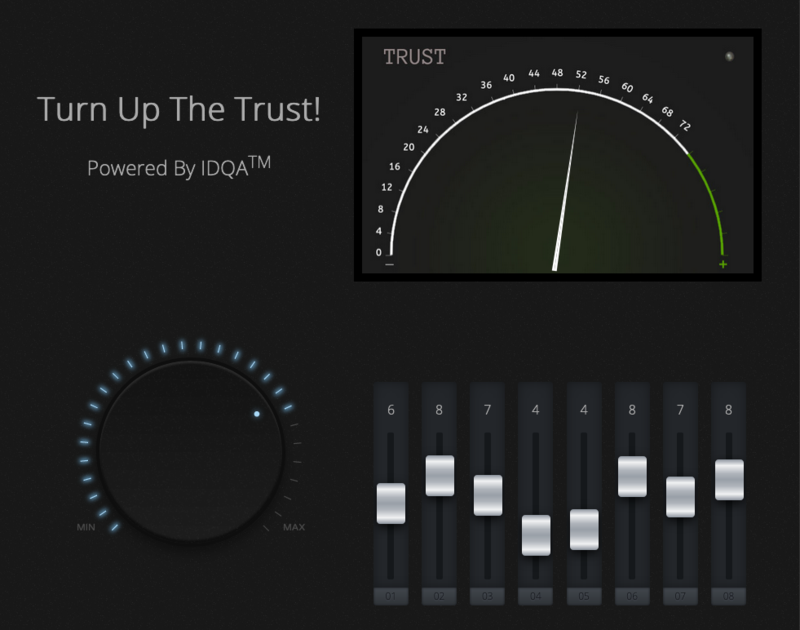
Turn Up the Trust
HOW RELIABLE is the identity claim represented by a credential?

Eight metrics measure a wide range of considerations, from original identity enrollment to the track record of the credential's use.
Relying parties, authentication gateways, and identity-sensitive transactions can require a minimum IDQA for access.

Access to individual metrics
The user's credential contains the total IDQA score (0-72) and the individual scores (1-9) of the eight metrics, allowing judgment on the relative importance of particular metrics.
For example, a seller in a multimillion-dollar real estate deal might require the buyer to have a high score on Metric 7 (assumption of liability) to protect against a fraudulent transaction, but a chat room for young girls might require a high Metric 2 score that ensures face-to-face enrollment, to protect against child predators joining the room. Relying parties can weigh the importance of metrics that are most relevant to their requirements.
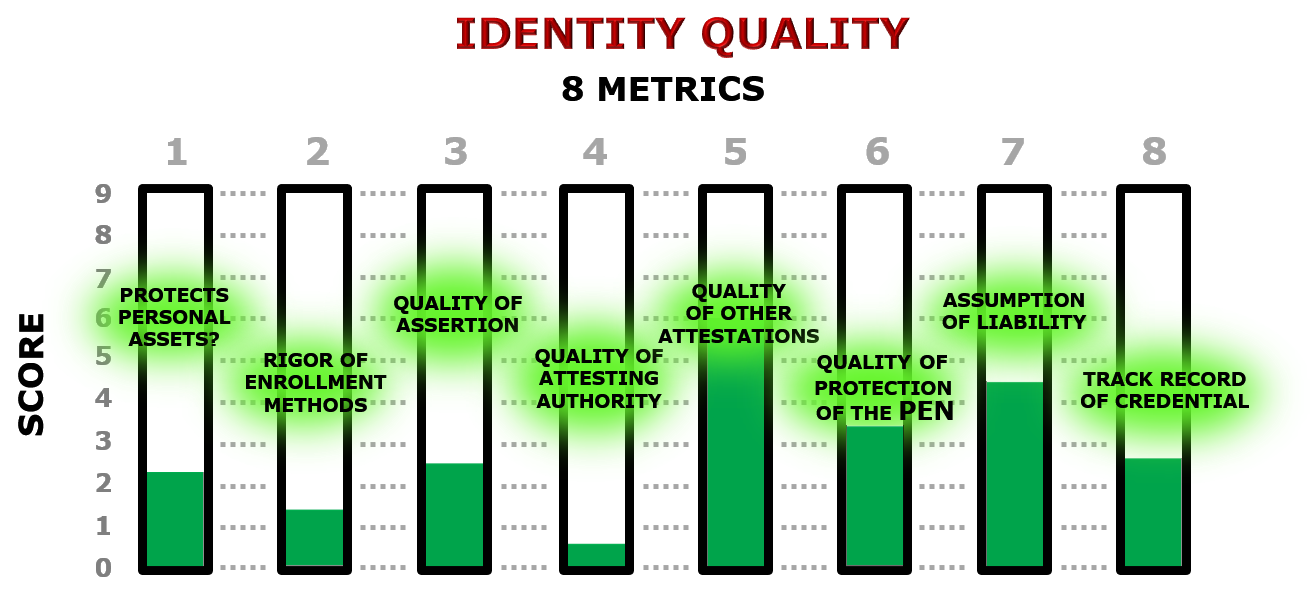
The eight metrics of Identity Quality™
Each scored on a scale of 0-9
-
1
Degree of linkage of personal assets
Does the user have "skin in the game" or are the sponsoring organization’s assets the only ones at risk? If the only reliable way to prevent credential sharing is to use credentials that protect the user's financial, reputational, and identity assets, then to what extent does the identity protect those personal assets including ownership of the credential itself?
-
2
Quality of enrollment practices
What type of enrollment procedure was used? Did it involve PII corroboration (“KBA”)? Was it face-to-face notarial or remote? How is provisioning performed? How is the process supervised and audited?
-
3
Variety of means of assertion
Does the credential support FIDO, Passkey, eIDAS, OpenID, and others? A well-used identity is a more reliable identity; the more places it is used, the better.
-
4
Quality of authoritative attestation
What source of authority attests to the validity of the assertion — that is, the claimed identity? Is the attesting party a certification authority? How reliable are their attestation practices? How is identity status reported: CRL, OCSP, or another method?
-
5
Attestations from others
In an enrollment interview, how many important online services is the subject able to authenticate to, with this credential or another?
-
6
Quality of the credential
What are the characteristics of the credential and its carrier? (Secure Element or Secure Enclave in a phone, crypto wallet, password manager, etc.) Is one key pair or token used for everything, or is there a “credential stack” allowing for different personas and different relying parties? Some risk profile / asset-value situations call for two, three, or four-factor hardware tokens or a one-time password, while a soft token in a client computer will suffice for others. How big are asymmetric keys: 1024, 2048, or 4096 bits?
-
7
Quality of assumption of liability
If fraud is committed with the use of the credential, who carries the liability? Is that commitment bonded? What are the terms of the bond? What is the source of funds for the fulfillment of the bond? Are there caveats or is the commitment absolute, regardless of the circumstances that made the credential available to the perpetrator? To protect assets and processes of the highest value, where a compromised identity would have the most serious consequences, civil and criminal liability should be involved in the issuance and ongoing use of the credential. Equally important is protection against fraudulent repudiation. Non-repudiation is the most difficult goal for a trust system to achieve, but the system must be useful to relying parties where significant transactions are involved.
-
8
Reputation of the credential
How long has the credential been used without revocation or reported compromise? How many transactions and authentication events has it been used for in total? The longer a credential has been used without incident, the more reliable it tends to be. Note that the reputation of the credential is not the same thing as the reputation of the person. For example, if someone with a very good reputation has a habit of lending his or her credential to family members and colleagues — resulting in documented confusion over who is responsible for what — then the reputation of the credential is diminished. Evidence of Nonduplication may also be assessed as part of the Reputation of the Credential.”